What is Pegasus and How Does it Impact Your Digital Security?
Security? Cybersecurity has become of great concern in the digital world, where life is entangled with devices. Among these, Pegasus is one of the most advanced spying cyber threats to be considered regarding the confidentiality of our digital data. In this elaborative article, we let ourselves into the world of Pegasus, showing its capabilities. Furthermore, we will also consider different measures to protect ourselves against its potential impact.
Table of Contents
Understanding the Capabilities of Pegasus
Pegasus is a highly advanced malware; it can bypass even the most robust security measures. The infection can happen through exploits on the device’s operating system, or social engineering, which may forcibly make the user click on some links. Once installed, Pegasus can reach a wide range of data stored on the device, including:
- Communication Data: Messages, emails, call logs, and even encrypted messaging apps like WhatsApp and Signal.
- Location Data: It will track location and movement, including the user’s location history.
- Multimedia Data: It grants them access to the device’s camera and microphone, enabling them to record audio and video.
- Device Information: It extracts information about the device, including contacts, calendar events, and browsing history.
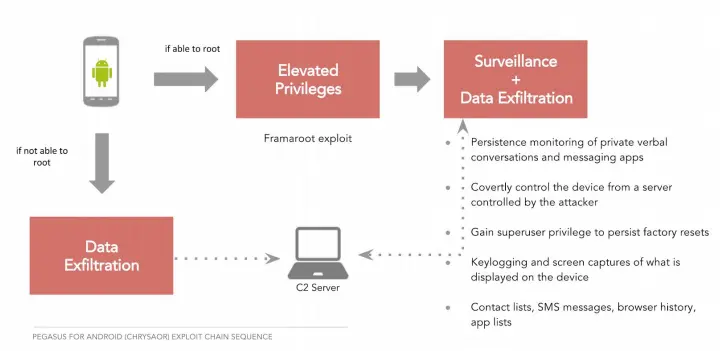
The extent of Pegasus’s capabilities is genuinely alarming. It can turn a user’s device into a surveillance tool, compromising their digital privacy and security.
More Information: Wikipedia
How Does Pegasus Infiltrate Devices?
Pegasus’s sophisticated infection methods normally include exploiting vulnerabilities in the device’s operating system. The most popular technique Pegasus uses in trying to infect devices is a “zero-click” attack. Such spyware can infect a device automatically, without any user interaction or intervention, by exploiting a weakness in any popular messaging app, such as WhatsApp or iMessage.
Also, Pegasus is propagated through phishing attacks: the user is induced into clicking on a malicious link or downloading a compromised file. Once the user interacts with the infected content, Pegasus will enter the device and initiate surveillance activities.
The Impact of Pegasus on Digital Security
The wide usage of Pegasus has changed the landscape of digital security and privacy. Hacking devices directly leads to the virus gaining access to an enormous amount of sensitive information, jeopardizing individuals, organizations, and even governments with Pegasus. The implication of what Pegasus can do is incredibly wide-ranging since it is so variedly applicable for the following malignancies:
- Targeted surveillance: Pegasus can be used to surveil targeted individuals in violation of their right to privacy and freedom of expression, including journalists, activists, and political dissidents.
- Corporate espionage: Pegasus can steal sensitive corporate data, such as trade secrets and intellectual property, implicating businesses regarding their security and competitiveness.
- State-Sponsored Spying: Pegasus has been implicated in state-sponsored spying, where governments and intelligence agencies use the software to conduct surveillance and gather intelligence from targets. This has raised concerns about power abuse and erosion of civil liberties.

The impact of Pegasus on digital security is undeniable, and it has become a pressing issue that requires immediate attention and action.
Cases of Pegasus Being Used for Surveillance
Pegasus has been associated with surveillance in several high-profile cases around the world. One such case targeted nationals of Mexico, where several journalists, activists, and even top government officials were monitored using Pegasus.
Another highly publicized incident was the targeting of Amazon founder Jeff Bezos. An investigation had been launched into an alleged hack of his phone using Pegasus, which eventually leaked his very personal information.
Recently, the whole world has been swept by the scandal over Pegasus. These back-to-back reports on using spyware to target political leaders, human rights activists, and journalists across many different countries have evoked widespread outrage and increased calls for greater accountability and regulation.
These cases are eloquent examples of the serious implications of Pegasus and the immediate need for strict measures to protect individuals and organizations from this potent invasive tool for surveillance.
Steps to Protect Yourself from Pegasus
The threat of Pegasus requires us to take proactive steps toward digital security. Here are some key things you can do to protect yourself from spyware:
- Keep Your Devices Updated: Keep your mobile devices updated to the latest versions of your operating system so that patches and vulnerabilities are updated.
- Be Cautious of Suspicious Links and Attachments: Be careful with links and attachments from suspicious messages. Never click on links or open attachments from an untrusted source, whether related to Pegasus or not. This can be one of the attack vectors that deliver Pegasus and other malware into your device.
- Use Secure Messaging Apps: Take extra care when selecting a secure messaging app. Consider using end-to-end encrypted messaging apps such as Signal or WhatsApp to keep your communications beyond surveillance.
- Regular malware scanning: Regularly scan your devices with any reputable antivirus or anti-malware software that can show evidence of Pegasus or other malware.
- Limit device permissions: Allow permissions to an application or service only where necessary. This might limit the data accessed through any imminent threat like Pegasus.
These are measures that, if implemented, would raise one’s level of digital security and reduce the possibility of becoming a target of Pegasus or some other advanced surveillance tools.
Pegasus and the Debate on Privacy vs. Security
The appearance of Pegasus restarted the discussion between sides for and against privacy versus security. On one side, governments and intelligence agencies say Pegasus-like tools are necessary to maintain national security and counter-terrorism. They want to argue that monitoring and tracking monitoring and tracking potential threats is part of what has been viewed as public safety.
However, civil liberties advocates and privacy experts view the use of Pegasus and other spy technologies as an increasingly dangerous erosion of individual privacy and human rights. They say that such unfettered use of powerful tools leads to a situation of abusing powers, targeting dissidents, and general pervasive state surveillance.
This debate underlines the dilemma of competing priorities that need to be weighed regarding individual privacy and the assurance of public safety. As Pegasus and other advanced surveillance technologies continue to evolve, finding a balance respectful of both privacy and security will require a meaningful dialogue among policymakers, technologists, and the public.
Pegasus Detection and Removal Tools
Because of this increasing threat of Pegasus, researchers and cybersecurity experts have developed several different tools and techniques that detect the presence of spyware and probably remove it from infected devices. Some of those are:
- Mobile Forensic Tools: Special software solutions, such as Cellebrite and Grayshift, are used to analyze mobile devices for traces of the Pegasus malware.
- Pegasus Detection Apps: Applications such as “Pegasus Spyware Detector” utilize machine learning algorithms to indicate the presence of Pegasus in a device.
- Pegasus Removal Guides: These include step-by-step directions and tutorials on removing Pegasus from the different mobile operating systems, such as iOS and Android.

While these utilities are bound to identify and mitigate the aftereffects of Pegasus, it should be stated that given the sophistication of spyware and the in-depth effort by developers to evade any detection continuously, it is quite tough to develop a fail-safe solution. The utilities and resources presented here can nevertheless be helpful for any individual or organization committed to safeguarding itself from Pegasus threats.
Government Regulations and Pegasus
The general use of Pegasus and related concerns about privacy breaches and human rights violations forced governments to act on the issue with corresponding regulations. Some major events unfolding in this context are:
- Export Controls: The United States, along with many other countries, had slapped export controls on Pegasus and a few other surveillance technologies, limiting their sale and distribution to certain entities and governments only.
- Investigations and Lawsuits: Investigations and lawsuits by governments and international organizations have also been launched against its use, and some countries have filed lawsuits against the NSO Group seeking accountability for misuse of the spyware.
- Legislation being proposed: Some governments are weighing or have proposed legislation regulating the development, sale, and use of surveillance technologies to protect individual privacy and civil liberties.
Although this development of regulations is a step in the right direction, given the complexity and constantly evolving nature of spyware like Pegasus, vigilance and collaboration between governments, technology companies, and civil society would still be required to deal with the challenge at hand.
Read Aslo: How to Handle a Traffic Ticket for Speeding in a Work Zone
Frequently Asked Questions
Q: What is it, and how does Pegasus work?
A: Pegasus is an extremely sophisticated spyware developed by Israeli cybersecurity company NSO Group. It is designed to infiltrate mobile devices and gather vast amounts of data, including messages, emails, location data, and audio-visual recordings.
Q: How does Pegasus access devices?
A: Pegasus has various ways of infecting a device. Still, most of its methods are through the device’s operating system vulnerabilities. Among those is one of the most widely used: a “zero-click” attack, in which the spyware may infect a device without any user interaction or intervention.
Q: What kind of data does Pegasus have access to on a compromised device?
A: It has access to a vast amount of data, such as communication logs, location data, multimedia content, device information, and more. It can turn the targeted user’s phone into an espionage tool, affecting digital privacy and security.
Q: How would I protect myself against Pegasus?
A: Since hacking with Pegasus requires an operating system or software vulnerability, keeping your device and software updated may prevent the infection. Other precautions against Pegasus include:
- Avoiding suspicious links and attachments.
- Using secure messaging apps.
- Regularly scanning for malware.
- Limiting permissions to apps and services.
Q: Is Pegasus legal? What’s being done to regulate it?
A: The use of Pegasus raises several concerns about infringement on citizens’ privacy and violation of human rights. Hence, many countries have enacted various regulations, including export controls and proposed legislation. However, due to the nature of surveillance technologies, finding effective ways and means of regulation and control is an uphill battle.
Conclusion
Pegasus is a frightening and disturbing disaster that has been our lot in our digital security and personal information. Its top-notch permissions to hack digital gadgets and expose an incredible quantity of sensitive information have wide, often expansive, implications for private individuals, organizations, and governments. As the debate continues on privacy versus security, we must proactively take concrete steps, coupled with raising our voice for strong regulations to curb the misuse of surveillance technologies like Pegasus.
By being informed and practising safety, we will engage in the endless discussion of this important issue: to build a future where at least our digital life is protected from prying eyes that are out to destroy our fundamental rights and freedoms.
I recommend reading the resources and tools listed in this article to get me started learning about Pegasus and how to protect my digital security. Be vigilant, and take care of your privacy in this digital age.