What Is an Accurate Description of Asymmetric Encryption Technology?
Strong, reliable encryption technologies could never be more critical than in the digital age, a modern society where information and data are the lifeblood. One of these encryption methods that has come to gain a lot of attention and wide adoption is the asymmetric encryption method, otherwise referred to as public-key cryptography. It is my great pleasure, as an experienced human writer, to delve deep into the details of this powerhouse in encryption technology and provide you with a truthful, precise explanation of its inner mechanics.
Table of Contents
Understanding the Basics of Encryption
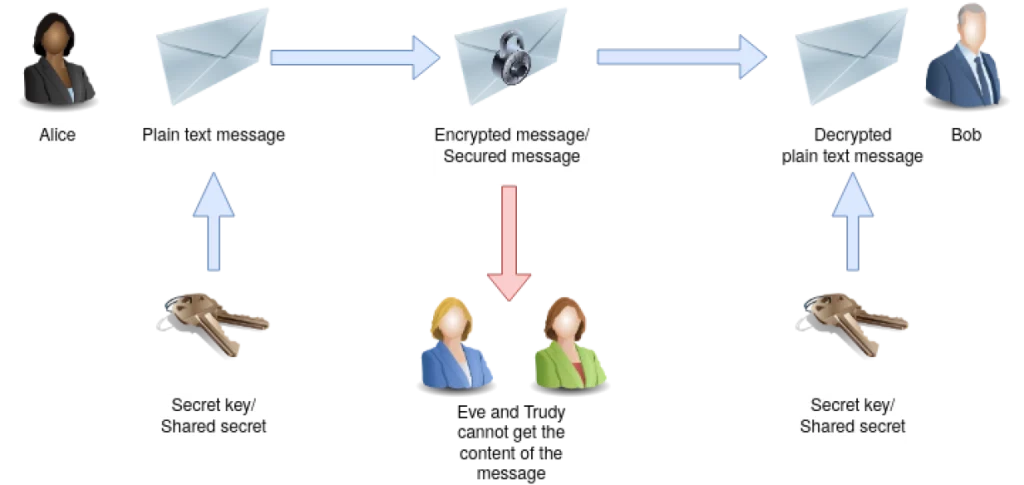
But before getting into the actual asymmetric encryption, let us talk about some of the very basics of encryption. It essentially designates a process for rendering readable information, or what is more technically referred to as plaintext, into an unreadable form, variously called ciphertext, under a previously defined algorithm and key. In this way, this information remains confidential and secure, even if it falls into the wrong hands.
Symmetric Encryption vs. Asymmetric Encryption
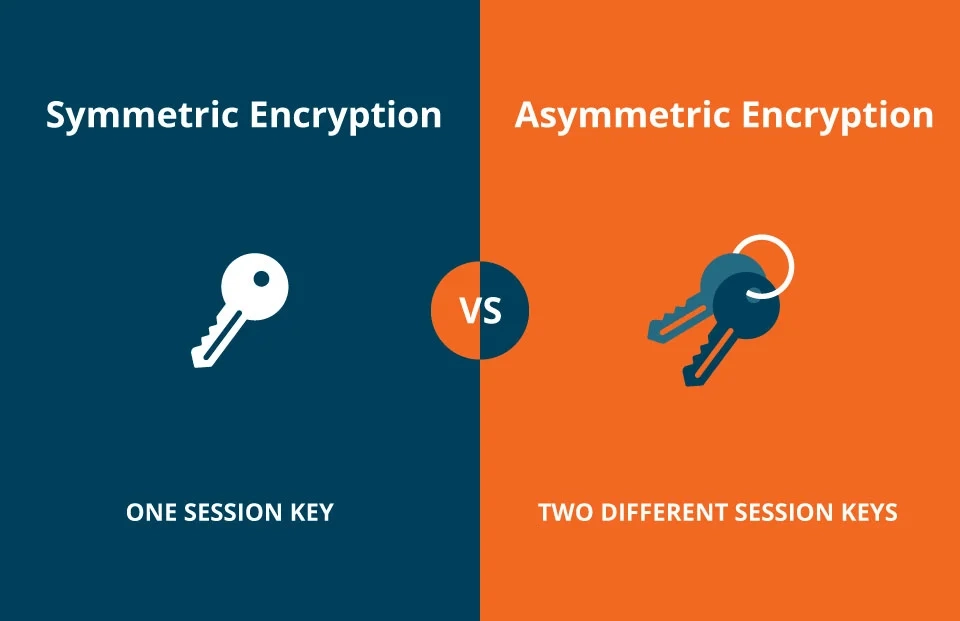
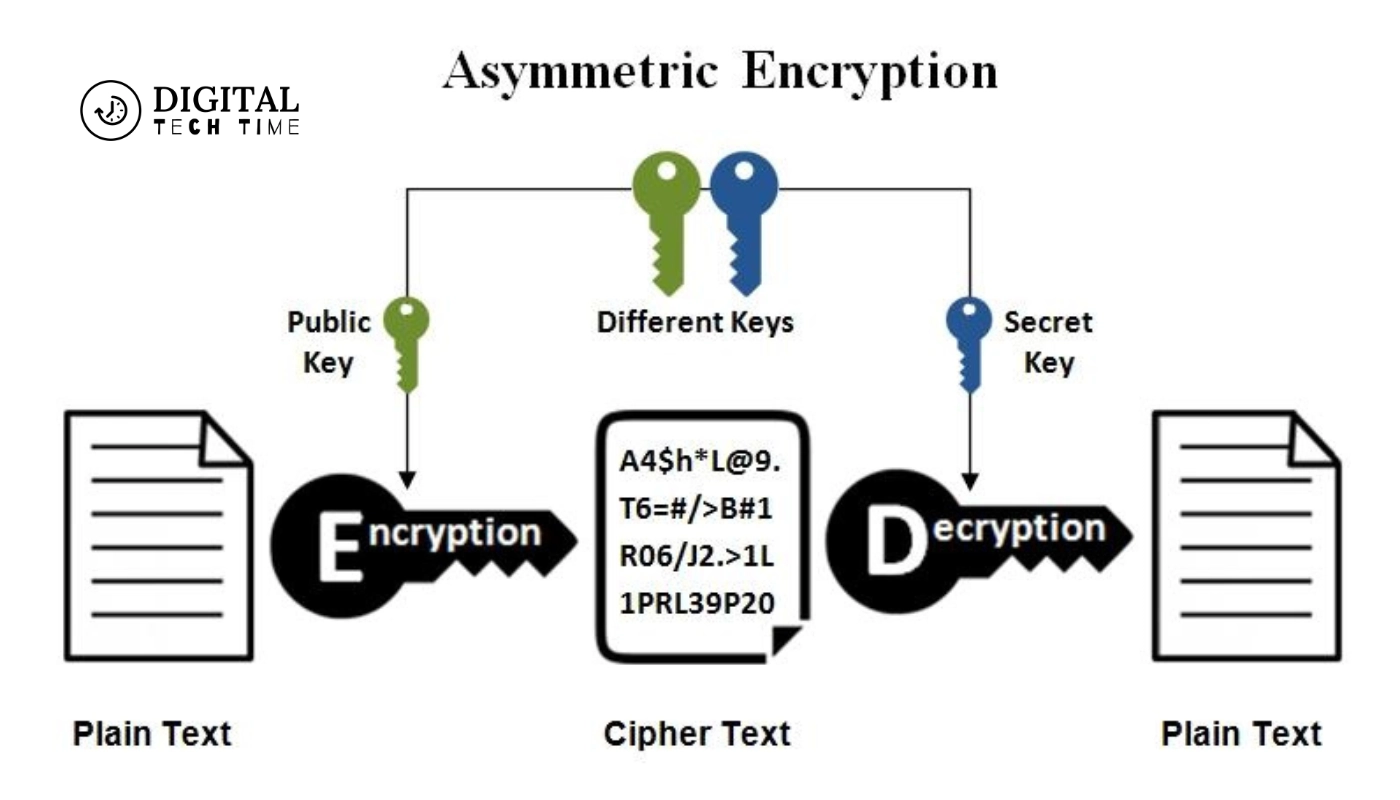
Broadly, there are two kinds of encryption techniques: symmetric and asymmetric encryption. In symmetric encryption, commonly referred to as secret-key cryptography, the same key is shared between the sender and the receiver to perform encryption and decryption. Asymmetric encryption uses a pair of keys belonging to the user: one public key and another private key. The public key is intended for enciphering, but the private key is for the reverse procedure, which is deciphering.
What is Asymmetric Encryption Technology?
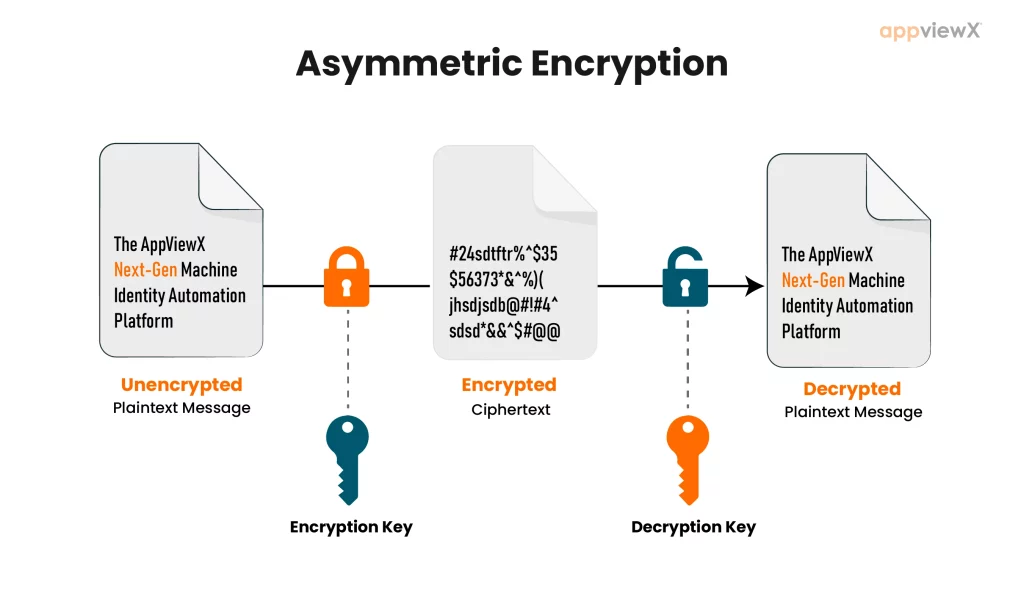
One of the very important asymmetric encryption technologies is public-key cryptography, a cryptographic system using a pair of mathematically related but different keys: a public and a private key. One key is public; the other one will remain private. The distinction between these keys is at the core of asymmetric encryption, which makes it different from symmetric encryption, which requires just a single shared key.
How Does Asymmetric Encryption Work?
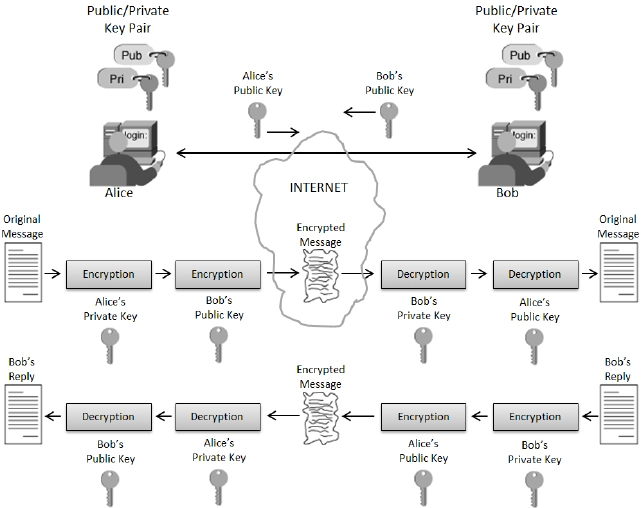
Asymmetric encryption is the concept behind it: it operates by using a pair of mathematically related keys. It uses the public key in the encryption and the private key in the decryption. The public key can be given to those who need to send encrypted recipient data. The private key is secret and withheld; generally, only the recipient knows it.
Key Components of Asymmetric Encryption
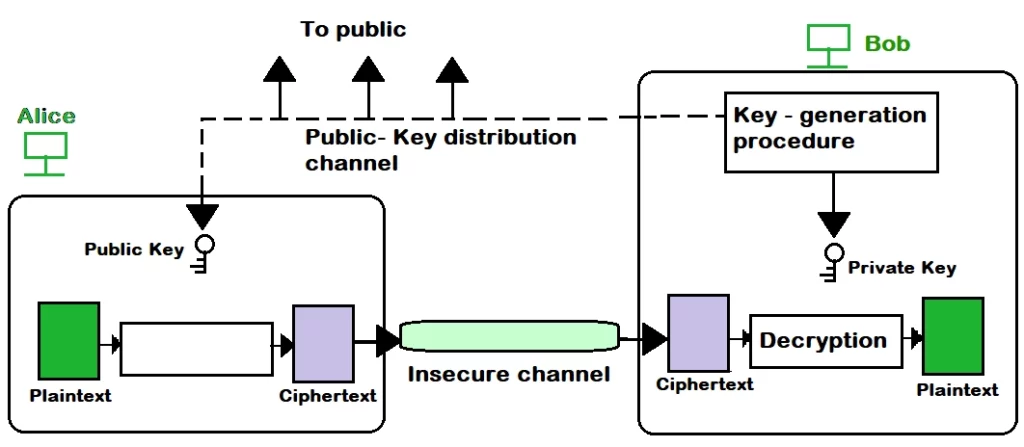
The key components of asymmetric encryption technology are:
- Public Key: This key is shared with anyone who wants to send encrypted data to the recipient. It is used for encrypting the data.
- Private Key: This key is kept secret and known only to the recipient. It is used to decrypt encrypted data.
- Key Pair Generation: The public and private keys are generated using a complex mathematical algorithm, such as RSA or Elliptic Curve Cryptography (ECC).
- Encryption/Decryption Process: The public key encrypts the data, and the private key decrypts it.
Advantages and Disadvantages of Asymmetric Encryption
Advantages of Asymmetric Encryption:
- Key Management: Asymmetric encryption simplifies key management by eliminating the need for a shared secret key between the sender and the receiver.
- Non-Repudiation: Asymmetric encryption provides non-repudiation, which means the sender cannot deny sending the encrypted data.
- Scalability: Asymmetric encryption is more scalable than symmetric encryption, as it does not require the distribution of a shared secret key to all parties.
Disadvantages of Asymmetric Encryption:
- Computational Complexity: Asymmetric encryption algorithms are generally more computationally intensive than symmetric encryption algorithms, which can impact performance.
- Key Size: Asymmetric encryption keys are typically larger than symmetric encryption keys, which can increase the storage and processing requirements.
- Vulnerability to Quantum Computing: Certain asymmetric encryption algorithms, such as RSA, are vulnerable to attacks by quantum computers, which could potentially break the encryption.
Real-world Applications of Asymmetric Encryption
Asymmetric encryption technology has found numerous real-world applications, including:
- Secure Communication: Asymmetric encryption is widely used in secure communication protocols, such as HTTPS, SSL/TLS, and S/MIME, to protect the confidentiality and integrity of data transmitted over the internet.
- Digital Signatures: Asymmetric encryption is the foundation for digital signatures, which are used to verify the authenticity and integrity of electronic documents and messages.
- Secure File Sharing: Asymmetric encryption protects the confidentiality of shared files and documents in cloud storage and file-sharing services.
- Secure Email: Asymmetric encryption is a crucial component of secure email protocols, such as PGP and S/MIME, which ensure the confidentiality and integrity of email communications.
- Secure Authentication: Asymmetric encryption is used in various authentication mechanisms, such as certificate-based authentication and public-key infrastructure (PKI), to verify the identity of users or devices.
Ensuring the Security of Asymmetric Encryption
Maintaining the security of asymmetric encryption technology is crucial, and several measures can be taken to ensure its integrity:
- Key Management: Proper key management, including the secure generation, storage, and distribution of public and private keys, is essential for the system’s overall security.
- Key Size: Using appropriately sized keys, based on the level of security required, can help mitigate the risk of brute-force attacks and other cryptanalytic techniques.
- Secure Algorithms: Utilizing well-established and cryptographically secure algorithms, such as RSA or Elliptic Curve Cryptography (ECC), is crucial for the long-term security of the encryption system.
- Regular Updates: Regularly updating the encryption software and protocols to address any known vulnerabilities or security issues is essential for maintaining the security of the system.
- Quantum-Resistant Algorithms: As the threat of quantum computing grows, exploring and adopting quantum-resistant encryption algorithms, such as lattice-based or hash-based cryptography, can help future-proof the security of asymmetric encryption systems.
Read Also: Secure Your Chats on iPhone
Frequently Asked Questions
Q: What is the difference between symmetric and asymmetric encryption?
A: The major difference between symmetric and asymmetric encryption lies in the key. Symmetric encryption uses only one shared key for encryption and decryption. On the other hand, the keys applied in asymmetric encryption are in pairs: one for encryption.
Q: How secure is asymmetric encryption?
A: Asymmetric encryption is generally considered more secure than symmetric encryption, as it eliminates the need for a shared secret key. However, the level of security depends on the specific algorithm used, the key size, and the implementation details.
Q: Can asymmetric encryption be broken?
A: While asymmetric encryption is highly secure, it cannot be said to be quite unbreakable. Some algorithms, like RSA, may be weak to attacks, especially with the ever-increasing speed of quantum computers. On this issue, regular updating and quantum-resistant algorithms are very important for maintaining the long-term security of asymmetric encryption systems.
Q: What are the real-world applications of asymmetric encryption?
A: Asymmetric encryption has numerous real-world applications, including secure communication, digital signatures, secure file sharing, secure email, and secure authentication.
Conclusion
It is, hence, in sum, that asymmetric encryption technology, otherwise called public-key cryptography, represents probably one of the strongest and most versatile encryption methods to have had a place in our digital landscape. Only through understanding the essential elements, tenets, and real-world applications of asymmetric encryption will we begin to appreciate its critical role in the confidentiality, integrity, and security of our digital communications and transactions.
This will enable an in-depth look into asymmetric encryption, seek practical applications, and provide follow-up through continued research in this fast-evolving domain. The more we understand and embrace these cutting-edge technologies, the better equipped we are to take on the forthcoming digital challenges of the future.