Why Is Anonymization A Challenge of Cybersecurity
In the digital age, where data reigns supreme, the concept of anonymization has emerged as a critical component of cybersecurity. As we navigate the intricate landscape of online interactions, the need to safeguard personal information has become paramount. Anonymization, the process of obfuscating or removing identifying details from data, stands as a pivotal technique in preserving privacy while enabling the secure exchange and analysis of sensitive information.
Table of Contents
Understanding Anonymization

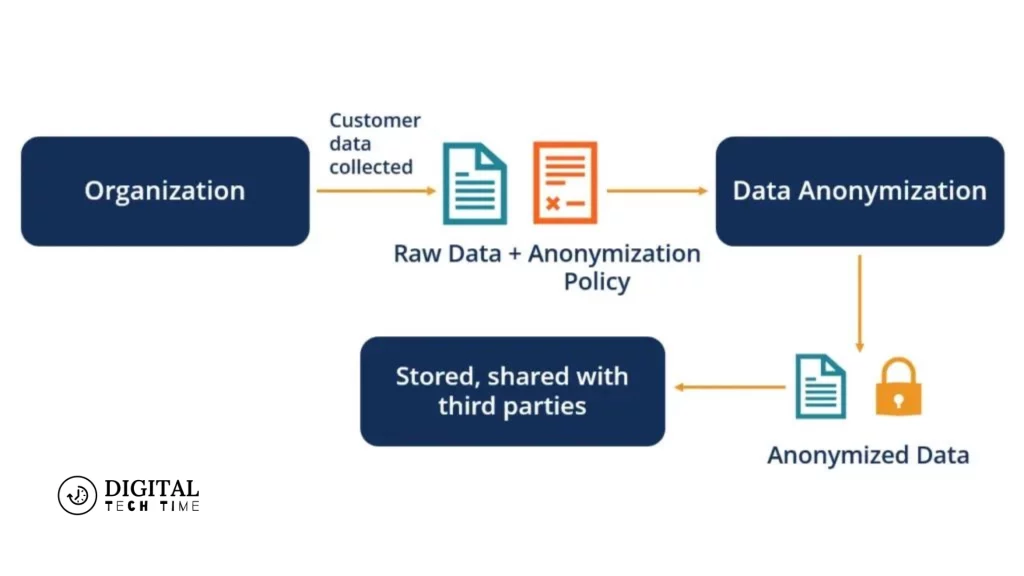
Anonymization is stripping away personally identifiable information (PII) from data sets, rendering the individuals associated with that data anonymous. This process involves carefully removing or obfuscating elements such as names, addresses, social security numbers, and other unique identifiers that could link the data back to specific individuals.
The primary objective of anonymization is to create a sanitized version of the data that can be shared, analyzed, or processed without compromising the privacy of the individuals represented within it. This technique is particularly crucial in healthcare, finance, and research, where sensitive information must be handled carefully to maintain confidentiality and comply with data protection regulations.
Privacy vs. Security: The Dilemma of Anonymization
At the core of the anonymization challenge lies a fundamental dilemma: balancing the need for privacy with the imperative of maintaining data integrity and security. On one hand, robust anonymization techniques are essential to protect individuals’ privacy and prevent unauthorized access or misuse of sensitive information. On the other hand, excessive obfuscation or removal of data elements can diminish the utility and accuracy of the information, hampering its intended purpose.
This delicate equilibrium requires a nuanced approach, where anonymization strategies are carefully tailored to each use case’s specific context and requirements. Striking the right balance is crucial to ensuring privacy and security objectives are met without compromising the integrity of the data.
Step-by-Step Guide: Implementing Anonymization Techniques
Adequate anonymization involves a multifaceted approach, encompassing various techniques and best practices. Here is a step-by-step guide to implementing anonymization strategies:
- Data Inventory and Classification: Begin by conducting a comprehensive inventory of the data sets within your organization. Classify the data based on sensitivity level and identify the elements requiring anonymization.
- Risk Assessment: Evaluate the potential risks associated with the data sets, considering factors such as the nature of the information, the intended use, and the potential consequences of a breach or unauthorized access.
- Anonymization Technique Selection: Choose the appropriate anonymization techniques based on the risk assessment and the specific requirements of your use case. Common techniques include:
- Data Masking: Replacing sensitive data with fictitious values or placeholders.
- Data Aggregation: Combining individual data points into summarized groups or categories.
- Data Suppression: Removing or redacting specific data elements.
- Pseudonymization: Replacing identifiable data with pseudonyms or codes.
- Differential Privacy: Adding controlled noise or perturbations to the data to protect individual privacy.
- Implementation and Testing: Implement the selected anonymization techniques consistently and accurately across all relevant data sets. Conduct thorough testing to validate the effectiveness of the anonymization process and verify that the resulting data meets the desired privacy and security requirements.
- Monitoring and Maintenance: Establish ongoing monitoring and maintenance procedures to ensure the anonymization process remains effective as data sets evolve and new threats or regulations emerge. Regularly review and update anonymization techniques as necessary.
Importance of Anonymization in Cybersecurity
The significance of anonymization in cybersecurity cannot be overstated. In an era where data breaches and cyber threats are rising, anonymization is a crucial defense against unauthorized access, identity theft, and other malicious activities. By obfuscating or removing sensitive information, anonymization minimizes the risk of exposing individuals’ details, thereby protecting their privacy and mitigating potential legal and reputational consequences for organizations.
Moreover, anonymization is vital in enabling secure data sharing and collaboration. By creating anonymized data sets, organizations can share information with trusted partners, researchers, or third-party service providers without compromising the privacy of the individuals represented in the data. This facilitates valuable insights, innovation, and collaborative efforts while maintaining compliance with data protection regulations.
Challenges of Implementing Anonymization
Despite its importance, implementing adequate anonymization has its challenges. One of the primary obstacles is the complexity of identifying and removing all potential identifiers within a data set. Seemingly innocuous data elements, when combined, can inadvertently reveal sensitive information, a phenomenon known as the “mosaic effect.”
Another challenge lies in balancing the trade-off between privacy and data utility. Excessive anonymization can render the data unusable for its intended purpose, while more anonymization may need to provide adequate privacy protection. Finding the optimal balance requires a deep understanding of the data, its intended use, and the associated risks.
Furthermore, the constantly evolving nature of cyber threats and data protection regulations poses an ongoing challenge. Organizations must stay vigilant and adapt their anonymization strategies to address emerging risks and comply with changing regulatory landscapes.
Strategies for Effective Anonymization
Organizations must adopt a strategic and proactive approach to overcome the challenges associated with anonymization. Here are some key strategies to consider:
- Comprehensive Data Governance: Implement robust policies and procedures defining roles, responsibilities, and processes for handling sensitive data. This includes establishing guidelines for data classification, anonymization techniques, and access controls.
- Privacy by Design: Embrace the principle of “Privacy by Design,” which involves integrating privacy considerations into the design and development of systems, products, and processes from the outset. This proactive approach helps to ensure that privacy and data protection are fundamental components rather than afterthoughts.
- Risk-based Approach: Adopt a risk-based approach to anonymization, where the level of anonymization applied is commensurate with the sensitivity of the data and the potential risks associated with its exposure. This targeted approach optimizes the balance between privacy and data utility.
- Continuous Training and Awareness: Invest in ongoing training and awareness programs to educate employees on the importance of anonymization, best practices, and the potential consequences of data breaches or mishandling of sensitive information.
- Collaboration and Knowledge Sharing: Foster collaboration and knowledge sharing within the cybersecurity community. Participate in industry forums, conferences, and working groups to stay informed about emerging threats, best practices, and regulatory developments related to anonymization.
- Continuous Monitoring and Improvement: Regularly review and update anonymization strategies and techniques to address evolving cyber threats, regulatory changes, and technological advancements. Continuously monitor the effectiveness of anonymization processes and implement improvements as needed.
The Future of Anonymization in Cybersecurity
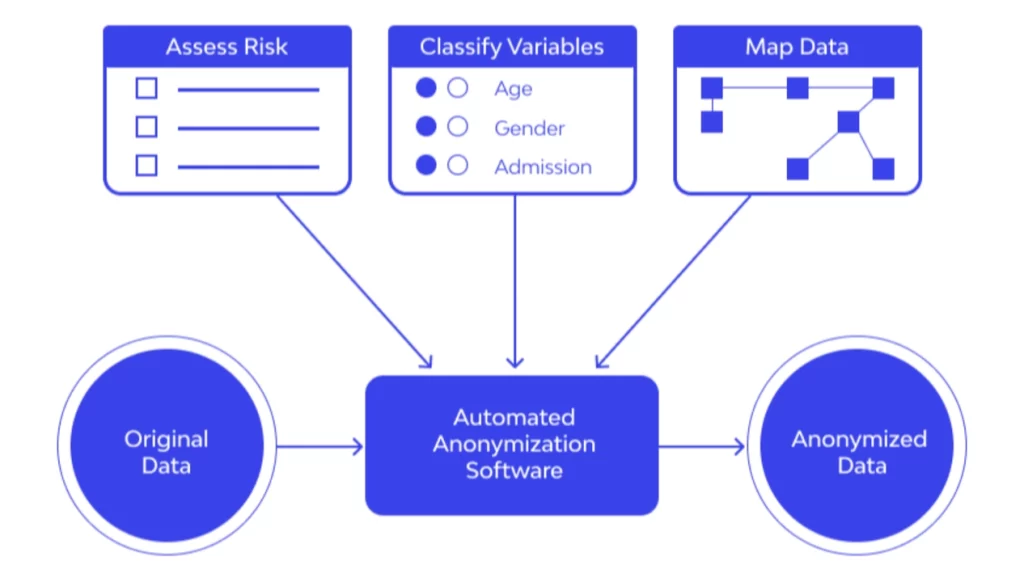
As the digital landscape continues to evolve, the importance of anonymization in cybersecurity will only grow. With the increasing volume and complexity of data, coupled with the ever-present threat of cyber attacks, organizations must remain vigilant and proactive in their approach to anonymization.
The future of anonymization will likely involve integrating advanced technologies, such as artificial intelligence (AI) and machine learning (ML). These technologies can aid in the automated identification and obfuscation of sensitive data elements, improving the efficiency and accuracy of anonymization processes.
Additionally, adopting emerging privacy-enhancing technologies, such as homomorphic encryption and secure multi-party computation, may provide new avenues for anonymization while preserving data utility and enabling secure collaborative analysis.
Related Post: The Role of Coding in Cybersecurity Careers
Frequently Asked Questions (FAQs)
What is the difference between anonymization and pseudonymization?
Anonymization involves completely removing or obfuscating identifying information, rendering the data anonymous. Pseudonymization, on the other hand, replaces identifiable data with pseudonyms or codes, allowing for the potential re-identification of individuals under certain circumstances.
Is anonymization a one-time process or an ongoing effort?
Anonymization is an ongoing effort that requires continuous monitoring and adaptation. As data sets evolve, new threats emerge, and regulations change, organizations must regularly review and update their anonymization strategies to maintain adequate privacy and security measures.
Can anonymized data be completely secure and risk-free?
While anonymization significantly reduces the risk of exposing sensitive information, it is essential to note that no anonymization technique is 100% foolproof. There is always a residual risk of re-identification, mainly when dealing with complex or high-dimensional data sets. Organizations must carefully assess and manage these risks through a comprehensive risk management approach.
How can organizations ensure compliance with data protection regulations when anonymizing data?
Compliance with data protection regulations, such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), requires a thorough understanding of these frameworks’ specific requirements and guidelines. Organizations should consult legal experts, industry best practices, and regulatory guidance to ensure their anonymization strategies align with applicable laws and regulations.
What role does employee training play in adequate anonymization?
Employee training and awareness are crucial components of an effective anonymization strategy. Organizations must invest in ongoing education and training programs to ensure employees understand the importance of anonymization, the techniques involved, and the potential consequences of data breaches or mishandling of sensitive information.
Conclusion
The challenge of anonymization in cybersecurity is a complex puzzle that demands a multifaceted approach and a deep understanding of the underlying principles. As we navigate the digital landscape, striking the delicate balance between privacy and security is paramount to maintaining trust, protecting individuals’ rights, and enabling secure data exchange and collaboration.